In this article from the “Datapedia” section, we will explore 4 pairs of terms, including Proxy and VPN. We will clearly explain when to use them, highlighting their definitions, purposes, use cases, and differences.
“Datapedia” is our monthly section where we explain the meaning of terms often misunderstood and confused in the world of Business Intelligence (BI) and Data Visualization.
Start enriching your vocabulary with this reading.
Data Engineer vs Data Architect: roles and responsibilities in the data universe
In the vast world of Information Technology, particularly in data management, two key roles emerge as fundamental pillars: the Data Engineer and the Data Architect.
The Data Architect is responsible for formulating the organizational data strategy and defining the standards and principles for data management across the entire organization. This role involves creating a “data blueprint” that guides other users in the implementation and use of data in accordance with the organization’s overall strategy. Data Architects must have extensive experience in databases, architecture, and data modeling, along with a deep understanding of data security principles.
The Data Engineer is the professional tasked with designing, maintaining, and optimizing the data infrastructure. This role involves creating pipelines to transform raw data into usable formats, while ensuring data accessibility and integrity. Data Engineers are experts in using tools for data integration and migration, as well as programming languages like Python. Moreover, with the increasing use of cloud services like AWS or Azure, Data Engineers must be proficient in implementing and using these platforms.
Comparison: Differences and Goals
While both roles operate within data management, their responsibilities and goals differ significantly. The Data Architect has a broader vision, defining the organizational data strategy and guiding the implementation of data management standards and principles. The Data Engineer focuses on the daily tasks of cleaning and preparing data, creating pipelines for data transformation and access.
In summary, while the Data Engineer focuses on implementing and optimizing data infrastructures, the Data Architect defines the organizational data strategy and guides its implementation. Together, these two roles collaborate to ensure that organizations fully leverage their data potential, enabling informed and strategic decisions.
Firewall vs Antivirus: how to defend yourself?
With an increasing number of services connected to the internet, the need to protect against potential risks and threats is growing. Two of the main solutions to keep your devices safe are firewalls and antivirus software. But what are they?
A firewall is a hardware or software defense device used to protect against potential attacks or intrusion attempts while browsing the internet. It acts as a filter for incoming and outgoing data from a computer connected to the internet, checking the reliability of the data and raising the security level of the system on which it is installed.
An antivirus is a software application that blocks, controls, and potentially removes other applications designed to attack and harm the system it operates on.
Comparison: Differences and Goals
Both firewalls and antivirus programs are tools used to protect a computer or device connected to the internet or another network. The difference lies in the type of protection they offer. A firewall is an external security measure, while an antivirus operates within the system. The firewall filters all network traffic, preventing the entry of infected files, malware, and viruses. In contrast, the antivirus aims to detect, disable, and remove malware and viruses already present on the computer or network.
Advantages, Limitations, and Use Cases
In an ideal world, a firewall alone would be sufficient to protect a computer from viruses and malware by blocking any potential risks upfront. However, firewalls can fail for various reasons, such as improper configuration or lack of updates. The same goes for antivirus software; it may not always have an updated list of malware and may not detect all threats in the system. Therefore, it is advisable to use both types of protection. The firewall provides an initial filter to prevent threats from reaching the system, while the antivirus intervenes in cases where the firewall fails by detecting and addressing the problems.
To sum up, an antivirus scans files on the computer or network to detect any viruses or abnormal behavior. In contrast, a firewall filters all internet traffic before it enters your network or computer and determines which elements are safe enough to access. Using both a firewall and antivirus together enhances the overall security of your system.
Proxy vs VPN: what to choose for secure browsing
For those who want to browse online securely while hiding their identity, there are two possible solutions: using a proxy or a VPN. But what are they, and what are the differences?
A proxy server is typically a remote public server accessed through a web application or desktop program that accesses web pages on behalf of the user.
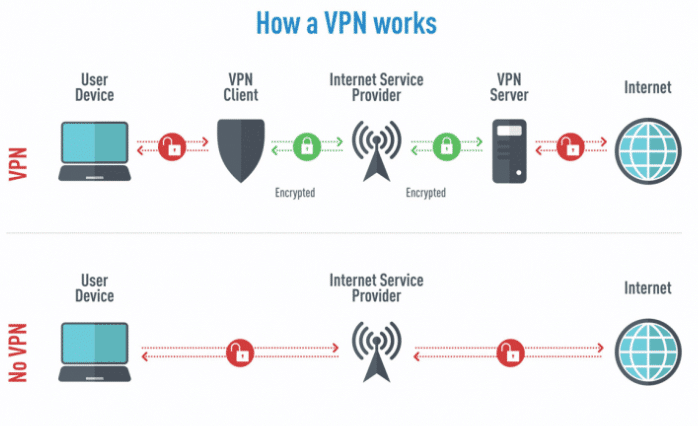
A Virtual Private Network, or VPN, is a private network that encrypts data sent or received from the internet. It helps access websites and use programs and applications securely and privately, regardless of the network used.
Comparison: differences and goals
A proxy allows the user to hide their IP address but does not offer additional protections. A proxy operates at the application level, so it can only redirect traffic within its scope. For example, changing the browser for navigation requires connecting to another proxy, and not all applications support its use.
A VPN, in addition to hiding the IP address, intercepts exchanged data and encrypts it, concealing information even from the user’s provider. Typically, a VPN operates at the operating system level, intercepting all incoming and outgoing traffic regardless of the application used. A VPN can also be installed on a router, operating at the network level and automatically protecting all connected devices.
Advantages, Limitations, and Use Cases
Proxies and VPNs represent two distinct approaches to enhancing online privacy and security, each with its own advantages and limitations. Proxies, known for their speed and configurability, are ideal for accessing geographically restricted content but offer limited security and leave traces of the user’s real IP address.
VPNs provide a higher level of security by encrypting all transmitted data and hiding the user’s real IP address, thus ensuring greater privacy and anonymity. However, this advantage can result in a reduction in connection speed.
In terms of use cases, proxies are often used to bypass geographic restrictions on websites or to improve access speed to web content, while VPNs are preferred for ensuring security and privacy when browsing on public Wi-Fi networks or accessing geographically restricted content.
To summarize, a proxy protects only the browser or a specific app, does not provide encryption, and is useful for anonymous browsing and changing IP addresses. A VPN, on the other hand, protects all data sent or received by the device or network, encrypts it, and is useful for changing the IP address, browsing anonymously, and protecting against attacks and targeted ads.
Browser vs Search Engine: how to navigate and find information online
Searching for information plays a crucial role in the decisions we make throughout the day. Two central tools for exploring the vast universe of the internet are the browser and the search engine. But what exactly are they, and how do they differ?
A Browser is a software application that allows users to access and view web pages on the internet. It functions as a gateway to the vast world of online information. Through the browser, users can type web addresses directly into the address bar or click on hyperlinks to explore different web pages. Besides displaying web pages, browsers offer various features, such as bookmark management, private browsing mode, and device synchronization.
A Search Engine is an online tool designed to help users find specific information on the internet. Users enter keywords or phrases into the search engine’s search bar, and the system returns a list of relevant results based on the search algorithms used. Search engines continuously analyze the vastness of the internet, indexing web pages and ranking them according to their relevance to user search queries.
Comparison: Differences and Goals
The primary difference between browsers and search engines lies in their function and purpose. A browser is a tool used to access and view online content, providing users with an interface to explore the web. A search engine focuses on searching and indexing online content, helping users find specific information among the vast array of available web pages.
Advantages, Limitations, and Use Cases
For instance, if you want to search for information on a specific topic using Google Chrome and Bing, you start by opening the Google Chrome browser on your device. Once opened, you type your search query directly into the browser’s address bar or click on the Bing search icon. Then, you enter the keywords related to your search, such as “best restaurants in my area.” After pressing the “Enter” key or clicking the search button, Bing displays a list of relevant results. You can then select an interesting result and click on it to access the corresponding website. While browsing the website, you can use Google Chrome’s features, such as automatic page translation, bookmark management, or incognito mode, to enhance your browsing experience and efficiently find the information you need.
In conclusion, both browsers and search engines are essential tools for navigating and finding information online. While browsers provide an interface to access and view web content, search engines offer an effective way to search for and discover specific information on the internet by indexing its content. By intelligently combining the use of both tools, users can maximize their online experience, easily finding the information they need.
Become an Expert in BI and Data Visualization
If you’re looking to learn the fundamentals of key BI tools or become an expert in Visual Analytics, discover our training programs.

Visualitics Team
This article was written and edited by one of our consultants.
Share now on your social channels or via email: